We engage collaboratively with your team to conduct in-depth discussions, analyze the infrastructure, and delineate the objectives for executing a Red Team Assessment, employing a comprehensive technical approach.
Seamless Integration With All Platforms
Our authentication & authorization APIs are fast, secure & well documented for ease of integration into any system, your organization's users (employees & customers) can login, logout & authorize themselves via our JWT token based apis to access your resources as per your set rules on the dashboard, providing you full visibility over their activities.
Private Blockchain Based Security
All your user's confidential data such as CRM credentials, employee code, login, logout time and other info safely secured on only place for your organization administrator to manage. Using above credentials the users can login into your systems & can go about doing their daily work while your APIs use BlockAuthority to authorize them everywhere in the system.
Organization Admin Dashboard
One stop place to manage all your users information with complete control over their activities, add new users as your team grows or delete them if required hence revoking their access to your system, you can block their account if you feel any suspicious activity or just sign them out with one click remotely through your dashboard.
BlockAuthority is built to protect your organization & users from all kinds of hackers, crackers & data theft

Customized Blockchain
You decide what data to store in blockchain, all the data remains out of reach of everyone except you. All of this data is served to you via our admin dashboard.
Activity Control
Feel any suspicious activity with any user account ? just log them out via our dashboard or just log everyone out if needed using global sign-out feature
Peace Of Mind Security
You & your users can use your systems without worrying about any info leak, theft or any sort of attack as our blockchain systems are 100% secure & monitored all the time.
Industry Standard APIs
All our APIs are JWT authentication based, easy to use & built for easy integration by developers following industry wide accepted practices.
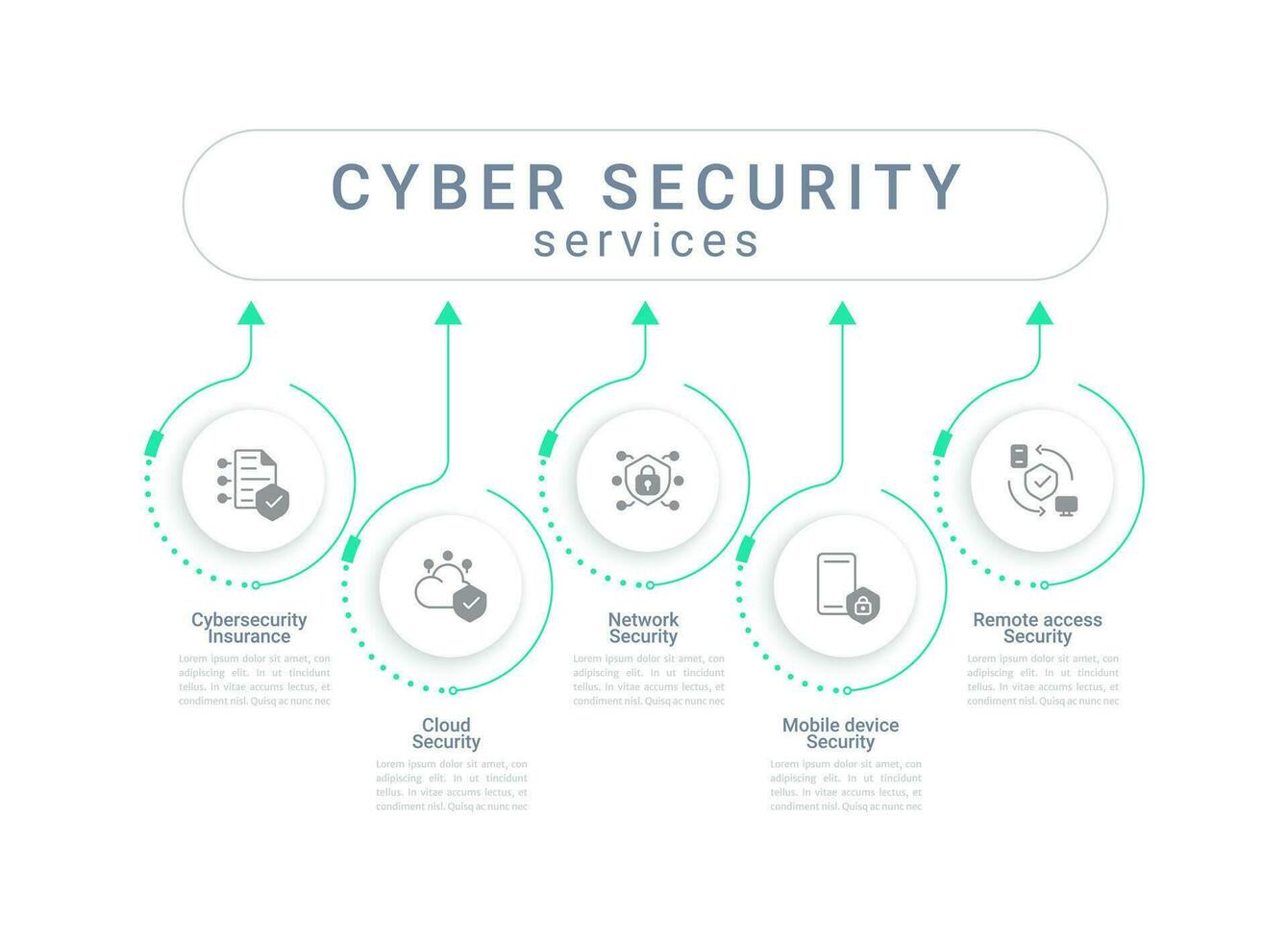
Optimize your cybersecurity for robust protection.
Network Security
We provide comprehensive network security solutions leveraging next-generation technologies that intelligently identify and proactively mitigate unknown threats in real time.
Endpoint Security
Endpoint Security Services deliver tailored, expert guidance for risk identification, solution implementation, and proactive threat prevention, instilling confidence in mitigating and thwarting future security threats.
Vulnerability Assessment And Penetration Testing
We employ proprietary methodologies in our penetration testing and vulnerability management services, grounded in established industry standards like OWASP and NIST, ensuring a comprehensive approach to security assessments.
SIEM
Nxgen's Managed SIEM service integrates cutting-edge Security Information and Event Management (SIEM) technology, seasoned security professionals, and real-time threat intelligence to augment threat visibility across on-premises, cloud, and hybrid environments.
RED TEAM ASSESSMENT SERVICES
Reconnaissance
In collaboration with your team, we conduct information reconnaissance pertinent to the assessment goals, preceding the strategic planning of a simulated, staged cyber attack.
Red Team Assessment
Upon identification of potential vulnerabilities, we proceed to conduct a verification assessment involving active intrusion attempts to validate and assess the security posture.
Reporting
The results of the assessment are compiled into a report detailing a summary of the test, vulnerabilities, risks detected, recommendations for bridging the GAP, and suggestions for better security.
Our team of experts delivers comprehensive and continuous 24/7 technical support services.
Product Consultation
We are committed to providing exceptional products and services in an efficient and technologically advanced manner, ensuring mutual benefit for us and our clients. Our guaranteed post-delivery support further solidifies our commitment.. .
01Security Consultation
We deploy precision-targeted strategies, integrating cutting-edge technologies and adhering to industry best practices to bolster digital defenses. Employing meticulous analysis, design, and implementation of robust security frameworks, our approach delivers proactive solutions that adeptly mitigate risks and defend against ever-evolving cyber threats in real-time.
0224/7 Technical Support
we recognize that the delivery of a product or service extends beyond its inception, and we place paramount importance on comprehensive post-delivery support. Our dedicated team ensures guaranteed 24/7 support, leveraging advanced technical expertise to address issues promptly and maintain optimal system performance post implementation.
03
Contact Us Today To Speak With An Expert About Your Specific Needs
Copyright © 2024 Nxgen Cysec



